Network Address Translation (NAT) is a method of mapping one IP address space into another by modifying network address information in the IP header of packets while they are in transit. i.e. Basically, for an IP packet in transit, the IP address is changed from one to another in a pre-determined manner.
Next question would be the need to translate (or map) one IP to another. There are multiple reasons for this translation as detailed below:
- Translation of private addresses into unique public addresses when accessing the Internet: Many organizations use private address space internal to the organization with a view of conserving the IP addresses. When a host with a private address needs to access another host across the Internet, the private address has to be mapped to a public IP address before sending the packet over the Internet. The reverse process takes place when the packet arrives from the public Internet addressed to a host withing the organization.
- Translation of addresses when transitioning internal addresses from one address range into another: Within an organization, some times need arises that an address range is mapped to another address range for compatibility reasons. For example, Company A acquires Company B, then the former may like to map the address range of the later for policy and compatibility reasons. NAT is used under such circumstances.
- When simple TCP load sharing is required across many IP hosts: Assume that you have an application server catering to the needs of the entire organzation and you would like to distribute the load across various such servers for faster response times, but the end-user sees only one server (IP address or host). In such cases, NAT allows you to distribute the load across several servers and and yet the users communicating to a single host.
Now that we know some of the cases where network address translation is useful, we discuss various types of NAT:
- Static NAT: Maps an unregistered IP address to registered IP (globally unique) addresses on one-to-one basis.
The command, ip nat inside source static <local ip> <global ip> configures address translation for static NAT. - Dynamic NAT: Maps an unregistered IP address to a registered (globally unique) IP address from a group of registered (globally unique) IP addresses dynamically. It is not necessary that a host gets the same IP address for the second time.
The command, ip nat inside source list <access-list-number> pool <name>is used to map the access-list to the IP NAT pool during the configuration of Dynamic NAT.
-
Overloading NAT:A special case of dynamic NAT that maps multiple unregistered IP addresses to a single registered (globally unique) IP address by using different port numbers.
Dynamic NAT with overloading is also known also as PAT (Port Address Translation). -
Overlapping NAT: When a host on your network is assigned an IP address that is on the same subnet as another device on the Internet or external network, the result is overlapping networks. It is possible to allow communication between two overlapping networks without having to renumber any devices by using Network Address Translation (NAT).
Below are some of key terms related to NAT which play important role in IP address Translations:
- Inside Local Address
- Inside Global Address
- Outside Local Address
- Outside Global Address
In the above term, first we break down the words Inside, Outside, Local, and Global for clarity.
- Inside = Under control of the customer. This will reside inside the customer network .
- Outside = Customer can’t control and reside outside the customer network.
- Local = Private addresses and refers to the address on the inside of your network.
- Global = Public IP addresses which are Globally routable addresses. This refers to the address on the outside of customer network.
Now we come back to the 4 key terms of NAT:
- Inside Local Address – Private addresses that customer can control. This is the IP address assigned to an end host on the inside network. The IP address is provided by the customer himself and is not required to be taken from IP address authority or Service provider.
- Inside Global Address – Public addresses that the customer can control. An example is the globally routable IP address(es) ISP provides to the organization (customer). A local address can’t traverse the Internet. Therefore, it needs to be translated to a global address before entering the global Internet. A packet with local IP address (generated on the local host) and destined for another host on the public Internet, needs to be translated to a routable public IP address given by the ISP.
- Outside Local Address – Private Addresses that are outside of customer’s control. This is the address that the inside hosts use to refer an outside host. The outside local address may be the outside host’s actual address or another translated private address from a different private address block. In other words – The IP address of an outside host as it is known to the hosts on the inside network.
- Outside Global Address – Public addresses that are outside of customer’s control.These are Globally Routable addresses and is the public IP address assigned to the end device on the other network to communicate over internet. For example, if an internal host is accessing Google mail server on the Internet, the address of the Google mail server would be the Outside Global address and you have no control on the IP assignment on Google mail server.
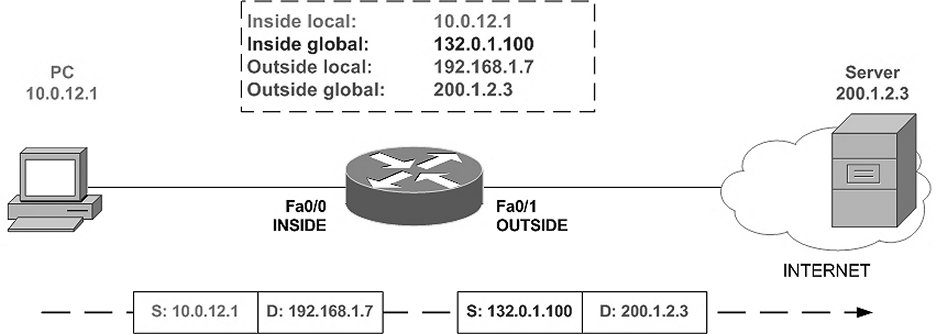
By looking at the figure above, we can interpret various addresses as below with respect to host 10.1.12.1 and outside host 200.1.2.3
- Inside Local address:10.1.12.1
- Inside Global address:132.0.1.100
- Outside Local address:192.168.1.7
- Outside Global address:200.1.2.3
As you can see Inside Local and Inside Global corresponds to the customer and Outside Local and Outside Global corresponds to the outside host. Some times it would be confusing if this point is not clear during the exam.
Ref.: http://www.ciscopress.com/articles/article.asp?p=1725268

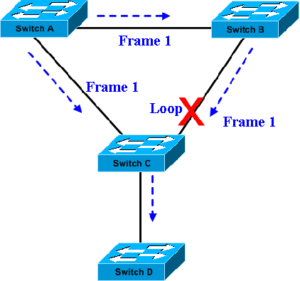 Assume that Frame 1 originating at SwitchA needs to reach destination SwitchD. As may be seen in the adjacent figure, Frame 1 originating a SwitchA has multiple paths to reach SwitchC. If the redundant path is not blocked, it may result in a loop. i.e. the same frame Frame 1 may be broadcast at SwitchC and again come back via SwitchB. Remember that bridges and layer-2 switches natively send frames to all ports other than the port on which the frame is received.
Assume that Frame 1 originating at SwitchA needs to reach destination SwitchD. As may be seen in the adjacent figure, Frame 1 originating a SwitchA has multiple paths to reach SwitchC. If the redundant path is not blocked, it may result in a loop. i.e. the same frame Frame 1 may be broadcast at SwitchC and again come back via SwitchB. Remember that bridges and layer-2 switches natively send frames to all ports other than the port on which the frame is received.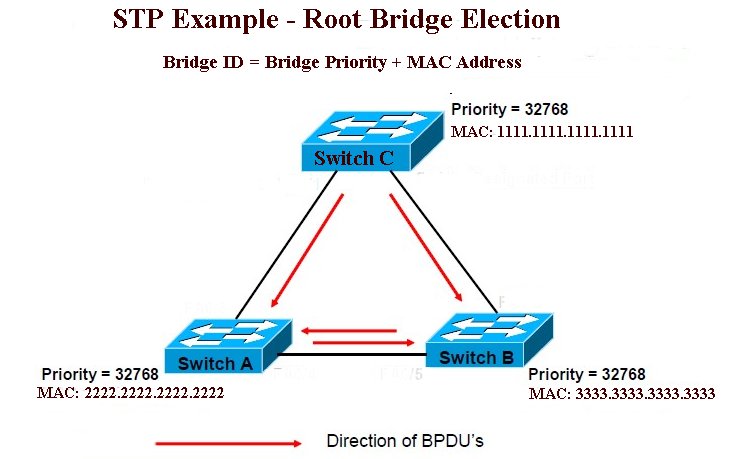 In the figure above, all the three switches (Switch A, Switch B, and Switch C) are propagating BPDUs as shown. The Root Bridge is not yet elected. Switch C has the lowest MAC address and hence elected as the Root Bridge (Bridge priorities are same for all three switches here, otherwise, Switch with higher priority value would have been elected as Root irrespective of the MAC addresses). The figure below shows the final network topology after STP convergence. Note that P05 port is blocked with the assumption that all links have same bandwidth.
In the figure above, all the three switches (Switch A, Switch B, and Switch C) are propagating BPDUs as shown. The Root Bridge is not yet elected. Switch C has the lowest MAC address and hence elected as the Root Bridge (Bridge priorities are same for all three switches here, otherwise, Switch with higher priority value would have been elected as Root irrespective of the MAC addresses). The figure below shows the final network topology after STP convergence. Note that P05 port is blocked with the assumption that all links have same bandwidth.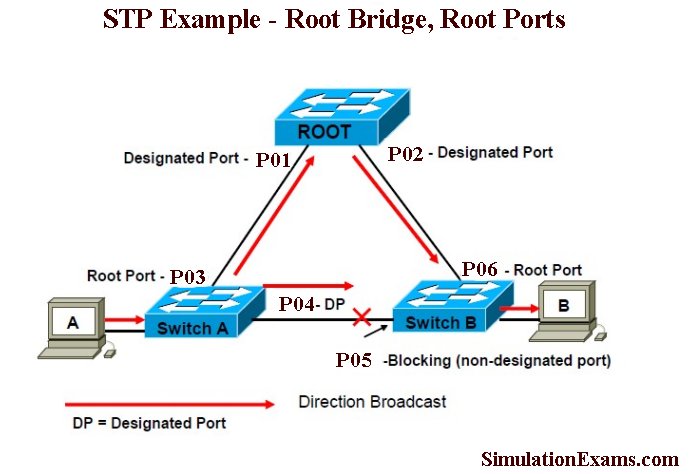
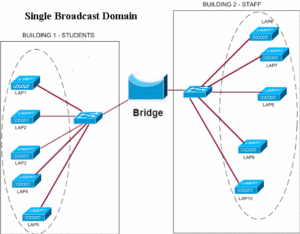
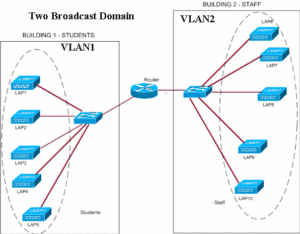 A router doesn’t forward broadcast traffic and therefore, users in VLAN1 will not be able to communicate with users in VLAN2, unless the router is configured to forward traffic from VLAN1 to VLAN2 and vice versa. As we can understand from the explanation above, configuring VLANs requires a layer-3 address mapping. Each VLAN in a VLAN network will have a unique IP address which would be used to identify the VLAN, and forward traffic from one VLAN to another VLAN. We can also use a Layer-3 Switch instead of a router for this purpose. The benefit of using Layer-3 switch is shorter response times.
A router doesn’t forward broadcast traffic and therefore, users in VLAN1 will not be able to communicate with users in VLAN2, unless the router is configured to forward traffic from VLAN1 to VLAN2 and vice versa. As we can understand from the explanation above, configuring VLANs requires a layer-3 address mapping. Each VLAN in a VLAN network will have a unique IP address which would be used to identify the VLAN, and forward traffic from one VLAN to another VLAN. We can also use a Layer-3 Switch instead of a router for this purpose. The benefit of using Layer-3 switch is shorter response times.

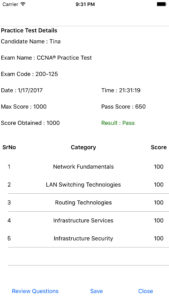 This screen shot shows the grade sheet that’s displayed after completion of the exam. As you can see, the percentage of marks is displayed for each topic as well as the aggregate. By viewing the topics that a candidate had performed poorly, one can improve the chances performing well in the actual exam.
This screen shot shows the grade sheet that’s displayed after completion of the exam. As you can see, the percentage of marks is displayed for each topic as well as the aggregate. By viewing the topics that a candidate had performed poorly, one can improve the chances performing well in the actual exam.
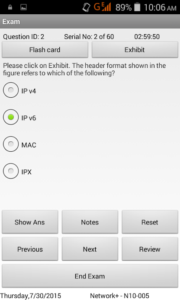 This screenshot provides the exam mode screen of the CCNA app. The question types include Multiple Choice Single Answer and Multiple Choice Multi Answer. Given in the figure is a MCSA question.
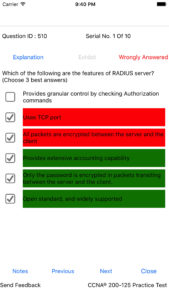
This screenshot provides the exam mode screen of the CCNA app. The question types include Multiple Choice Single Answer and Multiple Choice Multi Answer. Given in the figure is a MCSA question.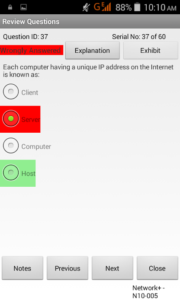 Shown beside is the review screen of the CCNA prep exam. This screen may be invoked after completion of the practice exam. As can be seen in the figure, your answer (in case it is wrong) is shown in red, and the right answer is shown in green color. The review of wrong answers after the exam is over, enables candidates to see where exactly he has made a mistake in answering the question.
Shown beside is the review screen of the CCNA prep exam. This screen may be invoked after completion of the practice exam. As can be seen in the figure, your answer (in case it is wrong) is shown in red, and the right answer is shown in green color. The review of wrong answers after the exam is over, enables candidates to see where exactly he has made a mistake in answering the question. Here, you select the mode of the practice test. Two available modes are Learn mode, and Exam mode. If you have just started you preparation, you can start with Learn mode. If you have finished with your preparation and like to feel how the actual exam, then take Exam mode.
Here, you select the mode of the practice test. Two available modes are Learn mode, and Exam mode. If you have just started you preparation, you can start with Learn mode. If you have finished with your preparation and like to feel how the actual exam, then take Exam mode.