4. Networking
4.2 Identify the basic Internet protocols and terminologies. Identify procedures for establishing Internet connectivity. In a given scenario, configure the operating system to connect to and use Internet resources.
1. Protocols and terminologies
3. Installing and Configuring browsers
4. Firewall protection under Windows XP
1. Protocols and terminologies
TCP/IP
E-mail (POP, SMTP, IMAP)
DNS: The Internet Domain Name System (DNS) offers a hierarchical naming scheme. DNS uses distributed lookup in which domain name servers map each domain name to an IP address or main exchanger address. Clients begin by trying to resolve names locally. When the local server cannot resolve the name, the client must choose to work through the tree of name servers iteratively or request the local name server to do it recursively.
HTML: It stands for Hyper Text Markup Language. HTML is the language used widely for constructing web pages. When you see a web page over the Internet, it contains HTML or a version of it. Other variations of HTML include XML, XHTML,
HTTP: Stands for Hyper Text Transfer Protocol. The HTTP protocol is a request/response protocol. A client sends a request to the server in the form of a request method, URI (Universal Resource Indicator), and protocol version, followed by a message containing client information over a connection with a server. The server responds with a status line, including the message's protocol version and a success or error code, followed by a server information, and possible entity-body content. HTTP communication normally uses port 80 of TCP/IP protocol suite.
HTTPS: This protocol is used for accessing a secure Web server where authentication and encrypted communication is required. Using HTTPS in the URL instead of HTTP directs the message to a secure port number (normally, port number 443) rather than the default Web port number of 80. The session is then managed by a security protocol. HTTPS encrypts the session data using the SSL (Secure Socket Layer) protocol. HTTPS is the preferred protocol when using credit card transactions.
An example format for secure URL is https://www.securesite.com
SSL: Secure Socket Layer is a protocol for encrypting and decrypting data across a secure connection from a client to a server. Both the client browser, and the server should support SSL for the communication to happen. The server is responsible for sending the client a certificate and a public key for encryption. Upon validation of the certificate, an SSL connection is established between the client and the server. Once a secure session is established, all data passing either side will be encrypted. Only the client and the server will be able to decrypt the data.
Telnet: This is another client-server protocol that emulates a terminal and used to execute commands on a server. You run commands on a server without leaving your client work station, as if you were working local to the server. Telenet uses port 23 of TCP. Typical telnet commands include ls, cd, md, etc.
FTP: FTP stands for File Transfer Protocol. Like any other protocol in TCP/IP suite of protocols, FTP is a client-server protocol for transferring files between a client and the server. FTP uses port number 21.
ISP: Short for Internet service provider. ISP is basically a service entity (business or organisation) that provides consumers access to the Internet and related services. ISPs maintain the infrastructure required for access to the Internet. The infrastructure may include DNS servers, mail servers, web servers, DHCP servers, remote access servers, etc. It is also important that the facility has redundant hardware/software for providing foolproof service. Major ISPs in US include MSN, EarthLink, AOL, etc.
2. Connectivity technologies
Dial-up networking: As the name suggests, it is used to connect a computer to an Internet service provider (ISP), or a remote computer through an analog modem and POTS (plain old telephone system).
The following are the important features of dial-up networking:
ISDN networking:
DSL networking: DSL stands for Digital Subscriber Line. DSL uses readily available telephone line for transmission of data to/from the Internet. Unlike dial-up Internet connection, a DSL connection will not tie up your telephone line. Though DSL uses the same telephone line, you can simultaneously make or receive telephone calls. DSL is normally, an always ON connection. You don't need to disconnect from the Internet when using DSL.
The two main categories of DSL for home subscribers are called ADSL and SDSL.
Cable : Broadband Internet connection that is designed to operate over cable TV lines is known as Cable Internet. It uses a modem, known as Cable modem for receiving and transmitting data between the client, and the ISP. Unlike DSL, Cable Internet uses shared medium. That is, all the subscribers connected to a given cable share the Internet bandwidth together. As a result, though the coaxial cable used by cable TV provides much greater bandwidth than telephone lines (used by DSL), the speeds achievable by Cable Internet are comparable to that of DSL.
As far as data privacy and security are concerned, DSL is preferred over Cable, due to the fact that data passing through cable is visible to all host computers connected over the same cable segment. DSL on the other hand uses a dedicated copper pair right from the telephone company up to the consumer. Therefore, the signals that flow through the copper wire are secure, and not shared over the media.
LAN: Stands for Local Area Networks. It is used for connecting two or more computers for the purpose of sharing resources. Two important versions of LANs are Peer-to-Peer networking, and Client-Server networking.
Windows 9x supports Peer-to-Peer networking.
Wireless
Satellite
3. Installing and Configuring browsers
Enable/disable script support
Enable JavaScript in Internet Explorer Version 5 and 6.:
1. In the Internet Explorer Menu go to Tools and then select Internet Options
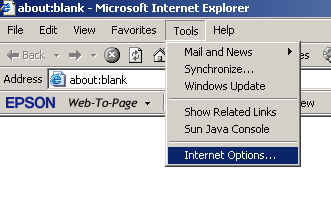
2. In the Internet Options window choose the Security tab
3. On the Security Window, choose Custom Level
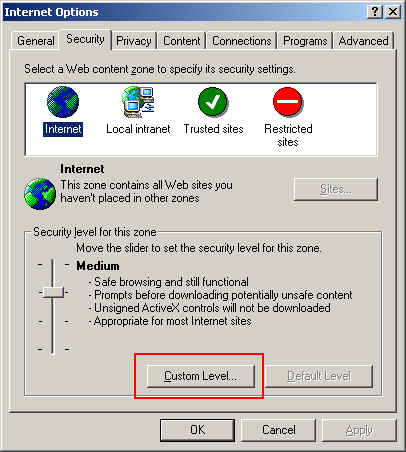
4. In the Settings window scroll down to Active scripting. Check Enable. Then Click on OK
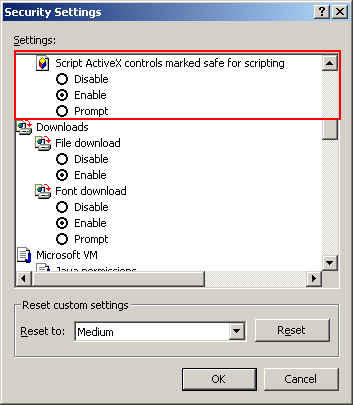
5. You will get a warning message. Click on Yes
6.On the Security Window, click OK.
Configure Proxy Settings
You may need to configure a Proxy server if not connected to the Internet directly. A proxy server protects your computer from external hacking, as well as allows a single Internet connection be shared among multiple computers.
For configuring Proxy, go to Tools in the main Menu of IE 6, and select Internet Options. In the resulting Window, select Connections.
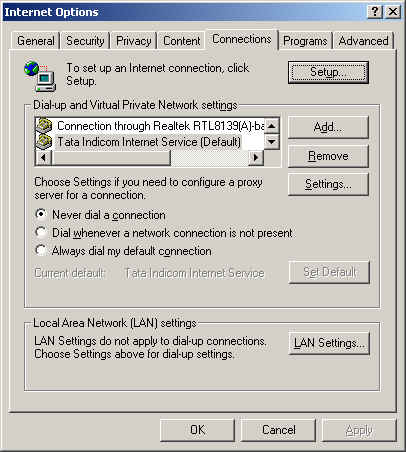
By clicking on "LAN Settings", another windows opens as shown below.
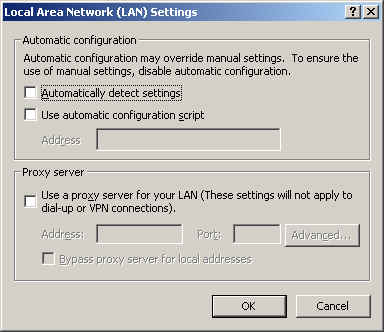
You can check the box titles "Proxy server", and enter the IP address, and Port number of the proxy server being used.
Configure security settings
Internet Explorer offers security zones including Trusted and Restricted zones. You can assign Web sites that you trust completely to trusted zones, and suspicious websites to Restricted Zones.
For configuring Proxy, go to Tools in the main Menu of IE 6, and select Internet Options. In the resulting Window, select Security.
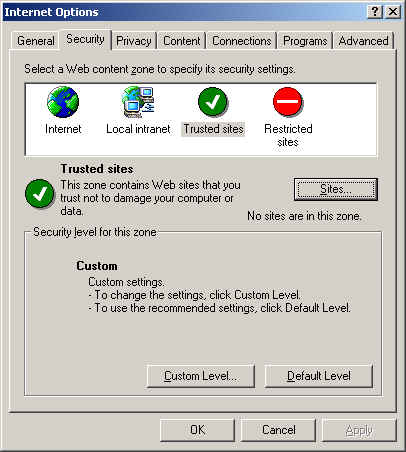
As seen in the above figure, you can choose "Trusted sites" and add some trust worthy sites there. Similarly, choose restricted sites, and add some sites that you think need to be restricted from viewing.
4. Firewall protection under Windows XP
Windows XP Internet Connection Firewall is a software that you can use to set restrictions on the information communicated between computer and the Internet. If your computer uses Internet Connection Sharing to provide Internet access to multiple computers, it is preferred to turn on Internet Connection Firewall on the shared Internet connection.
To enable or disable Internet Connection Firewall
1.Open Network Connections
2.Click the LAN, Dial-up, or High-Speed Internet connection that you want to protect, and then, under Network Tasks, click Change settings of this connection.
3.On the Advanced tab, under Internet Connection Firewall, select one of the following:
Note that you should not use ICF when connecting to the Internet using Virtual Private Network (VPN). You require administrative privileges to enable or disable ICF.
Disclaimer: Simulationexams.com is not affiliated with any certification vendor, and Sim-Ex™ Practice Exams are written independently by SimulationExams.com and not affiliated or authorized by respective certification providers. Sim-Ex™ is a trade mark of SimulationExams.com or entity representing Simulationexams.com.A+™ is a trademark of CompTIA® organization.