Description: This exercise helps to know about various physical security methods and their features.
Instructions:
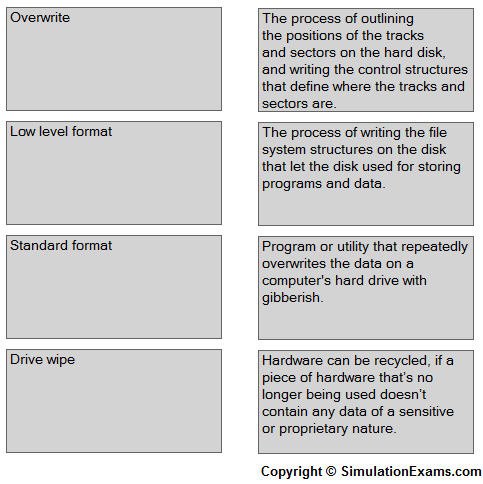
1.Various data destruction/disposal methods are given on the column A
2.Their features are given on the column B
3. Match (drag and drop) the data destruction/disposal methods given on Column A with their appropriate feature given on the column B.
Explanation:
A low-level format (typically only accomplished in the factory) can be performed on the system, or a utility can be used to completely wipe the disk clean. This process helps ensure that information doesn’t fall into the wrong hands.
Standard format: The process of writing the file system structures on the disk that let the disk used for storing programs and data.
Overwrite: Overwriting the drive entails copying over the data with new data. A common practice is to replace the data with 0s. A number of applications allow you to recover what was there prior to the last write operation, and for that reason, most overwrite software will write the same sequence and save it multiple times.
Drive wipe: a piece of hardware that's no longer being used doesn't contain any data of a sensitive or proprietary nature, that hardware can be recycled (sold to employees, sold to a third party, donated to a school, and so on). That level of assurance can come from wiping a hard drive or using specialized utilities.
Note: Please refer to the SimulationExams.com Sim-Ex Lab Simulator for A+ software to try complete lab with instructions.
Disclaimer: Simulationexams.com is not affiliated with any certification vendor, and Sim-Ex™ Practice Exams are written independently by SimulationExams.com and not affiliated or authorized by respective certification providers. Sim-Ex™ is a trade mark of SimulationExams.com or entity representing Simulationexams.com.A+™ is a trademark of CompTIA® organization.